EDR – Endpoint Detection and Response
Our EDR services provide deep visibility and rapid response capabilities for your endpoints — desktops, laptops, servers, and mobile devices. With MSP knowledge of your infrastructure and MSSP-grade detection, we neutralize threats before they spread.

🔍 Continuous Endpoint Monitoring


We collect and analyze endpoint telemetry in real-time to detect suspicious behavior, ransomware activity, policy violations, and advanced threats.
Intelligent Endpoint Defense with Expert Oversight
Features:
Process, file, registry, and network monitoring
AI-driven threat detection and alert scoring
Behavioral analysis and anomaly detection
Local and cloud-based sensor deployments
Rapid Threat Containment & Response
We isolate compromised devices, kill malicious processes, and take immediate remediation actions — without waiting for manual intervention.
Features:
One-click endpoint isolation
Remote shell for investigation
Automated and analyst-assisted response
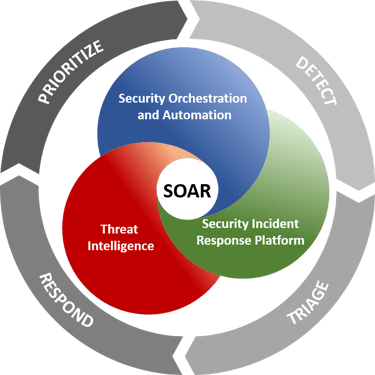
Integration with SOAR and ticketing systems

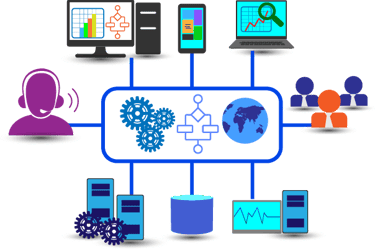
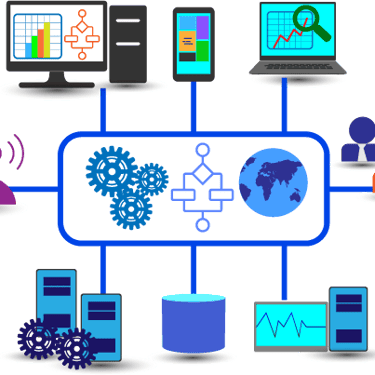
MSP + MSSP EDR Integration
Features:
MSP Benefit: EDR integrates with your patch management, helpdesk, and RMM tools
MSSP Benefit: Our SOC monitors and responds 24/7 to alerts from your endpoints
Outcome: Better visibility, faster containment, less business impact
Threat hunts based on MITRE ATT&CK
Search for indicators of compromise (IoCs)
Tailored alert tuning per environment
Weekly or ad hoc hunt reports
Proactive Threat Hunting on Endpoints
We don't wait for alerts — we search for early signs of compromise across all endpoints.
✅ Business Outcomes
Stop ransomware, phishing, and insider threats at the endpoint
Reduce dwell time and contain infections quickly
Lower IT workload with automated and expert-led response
Achieve compliance through endpoint visibility and control
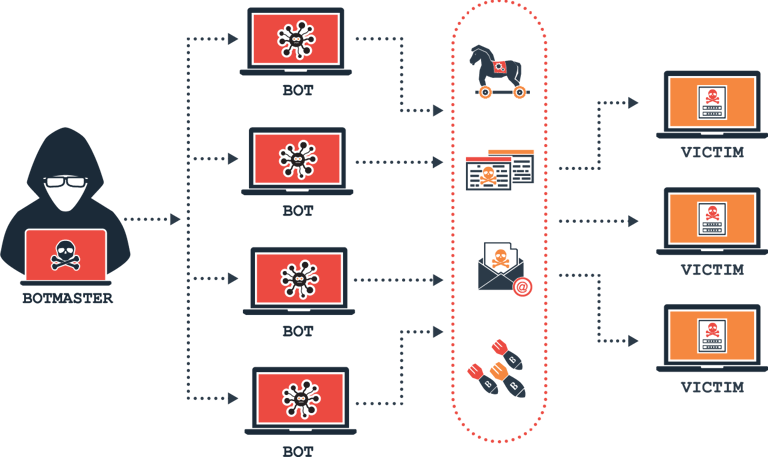
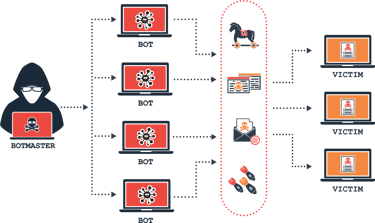

Remediation & Recovery
EDR isn’t just detection — we help you return systems to a known-good state with minimal downtime or data loss.

🔍 Continuous Endpoint Monitoring


Features:
Rollback of malicious changes
Malware removal and registry clean-up
Forensic evidence collection and root cause tracing
Post-incident reporting and lessons learned
We collect and analyze endpoint telemetry in real-time to detect suspicious behavior, ransomware activity, policy violations, and advanced threats.
Intelligent Endpoint Defense with Expert Oversight
Features:
Rollback of malicious changes
Malware removal and registry clean-up
Forensic evidence collection and root cause tracing
Post-incident reporting and lessons learned
IT Services Available
Managed IT Services (MSP)
Desktop & workstation support
Server support & maintenance
Patch management
Backup & disaster recovery
Website Design & Development
Cybersecurity (MSSP)
Wi-Fi installation / optimization
Switches, firewalls, routers
Network security
Cabling & infrastructure
24/7 SOC monitoring
Compliance readiness
Phishing protection
Website Security & Hardening
SIEM, EDR, MDR, firewall management
Physical Security
Video surveillance
Access control
Intercom & audio security
Body Worn Cam
Microsoft 365 management
Google Workspace
AWS cloud
Cloud backup & email security
Web Hosting & Maintenance
E-commerce Setup & Integration
Business phone systems
Call routing, auto-attendants
Remote / hybrid calling
Migrations
Unified Communications / VoIP
Networking & Infrastructure
Cloud Services
📞 Ready for Better IT Security Support?
Get fast, friendly, expert help — backed by enterprise-level security.