Identity & Access Management (IAM)
As both an MSP and MSSP, we deliver IAM solutions that simplify user lifecycle management while enforcing zero-trust access policies across your organization. From provisioning and MFA to privileged access and identity governance, our team ensures that only the right people access the right resources — at the right time.
🧾 Identity Lifecycle & Provisioning


Features:
SSO (Single Sign-On) and federated identity
Role- and attribute-based provisioning
Active Directory & Azure AD integration
MSP-friendly automation tools for HR/IT sync
Automate onboarding, offboarding, and role-based access control across cloud and on-premise systems.
Secure Access Starts with Smart Identity


Multi-Factor Authentication (MFA) & Access Control
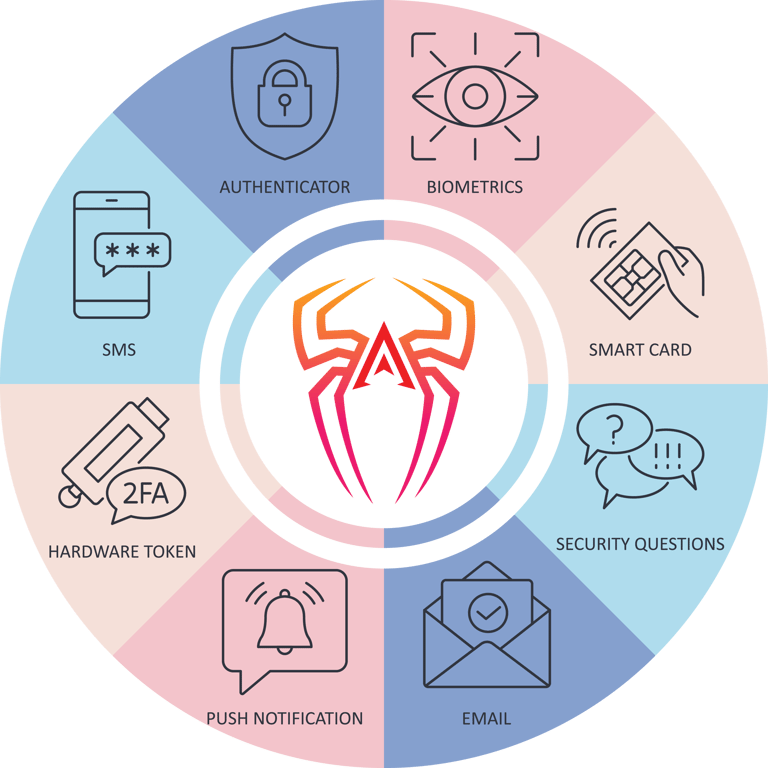

Features
Protect identities with strong authentication and conditional access policies tailored to your business.
Cloud and VPN MFA enforcement
Geo/IP/device-based conditional logic
MFA integration with SaaS and legacy apps
Self-service password reset and lockout protection
Privileged Access Management (PAM)


Managed Security Services Built for Modern Threats
Protect identities with strong authentication and conditional access policies tailored to your business.
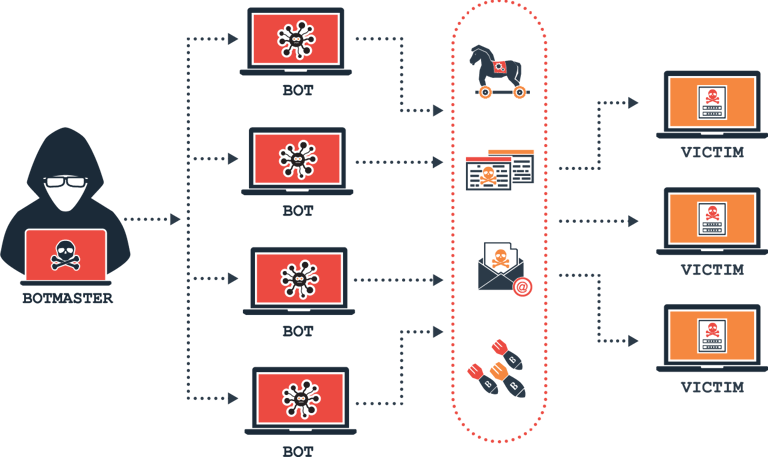
Features:
SSO (Single Sign-On) and federated identity
Role- and attribute-based provisioning
Active Directory & Azure AD integration
MSP-friendly automation tools for HR/IT sync
MSP + MSSP-Driven IAM Delivery
✅ Business Outcomes
We bridge IAM between IT operations and cybersecurity:
MSP: Simplify user management and access deployment
MSSP: Monitor, analyze, and respond to identity-based threats
Reduce help desk load with self-service & automation
Prevent unauthorized access and lateral movement
Enforce least privilege with confidence
Streamline audits and compliance reviews

Identity Governance & Compliance

Aligned with Industry and Regulatory Standards
Meet compliance requirements through visibility, auditing, and entitlement reviews


Access certification and attestation workflows
Identity analytics and risky login detection
Integration with GRC, SIEM, and SOC alerts
Compliance alignment: HIPAA, SOX, NIST, ISO 27001
We Support:
📞 Ready for Better IT Support?
Get fast, friendly, expert help — backed by enterprise-level security.


