MDR – Managed Detection and Response
Our MDR services combine the power of cutting-edge threat detection technologies with the vigilance of 24/7 human-led response. As your MSP and MSSP partner, we integrate with your IT environment to detect, investigate, and contain threats — before they become breaches.


💡 24/7 Threat Monitoring and Detection


Endpoint, network, and user behavior monitoring
Threat detection powered by AI and MITRE ATT&CK
Anomaly detection and suspicious activity correlation
Fully managed by our SOC experts
We continuously monitor endpoints, servers, and network activity for signs of compromise, leveraging real-time telemetry, AI analytics, and curated threat intel.
Advanced Threat Detection. Expert-Led Response
Features
Incident Response & Containment
We act fast to contain threats through isolation, credential revocation, and remediation — collaborating with your IT team at every step.
Features
Endpoint isolation and containment
Playbook-driven response workflows
Support for EDR, SIEM, and SOAR integration
Executive-level post-incident summaries

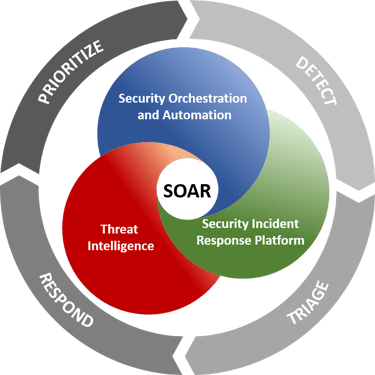

Threat Hunting & Behavioral Analysis
Our analysts proactively search for hidden threats that bypass traditional defenses, using both automated tools and human expertise.
Features
Hypothesis-based and IoC-driven threat hunting
UEBA (User and Entity Behavior Analytics)
Root cause analysis and lateral movement tracking
Weekly or monthly threat hunt reports
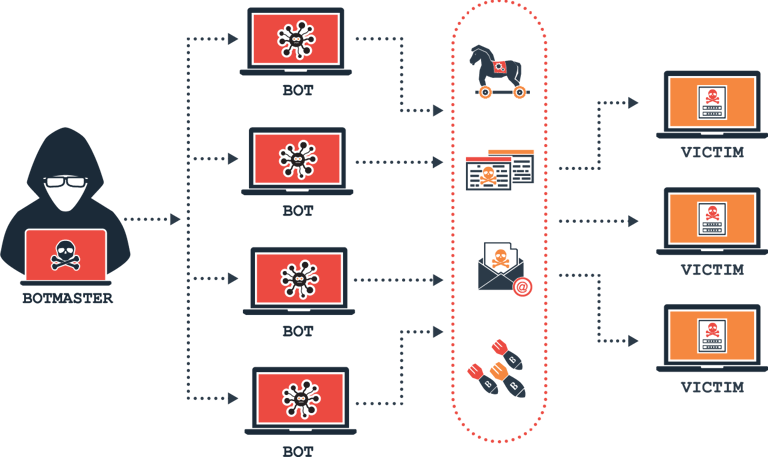
Rapid Threat Containment & Response
We isolate compromised devices, kill malicious processes, and take immediate remediation actions — without waiting for manual intervention.
One-click endpoint isolation
Remote shell for investigation
Automated and analyst-assisted response
Integration with SOAR and ticketing systems
Identity Governance & Compliance

Aligned with Industry and Regulatory Standards
Meet compliance requirements through visibility, auditing, and entitlement reviews


Access certification and attestation workflows
Identity analytics and risky login detection
Integration with GRC, SIEM, and SOC alerts
Compliance alignment: HIPAA, SOX, NIST, ISO 27001
We Support:
📞 Ready for Better IT Support?
Get fast, friendly, expert help — backed by enterprise-level security.


